Got IT issues slowing you down? We provide both on-site and remote support across Australia, so help is never far away.
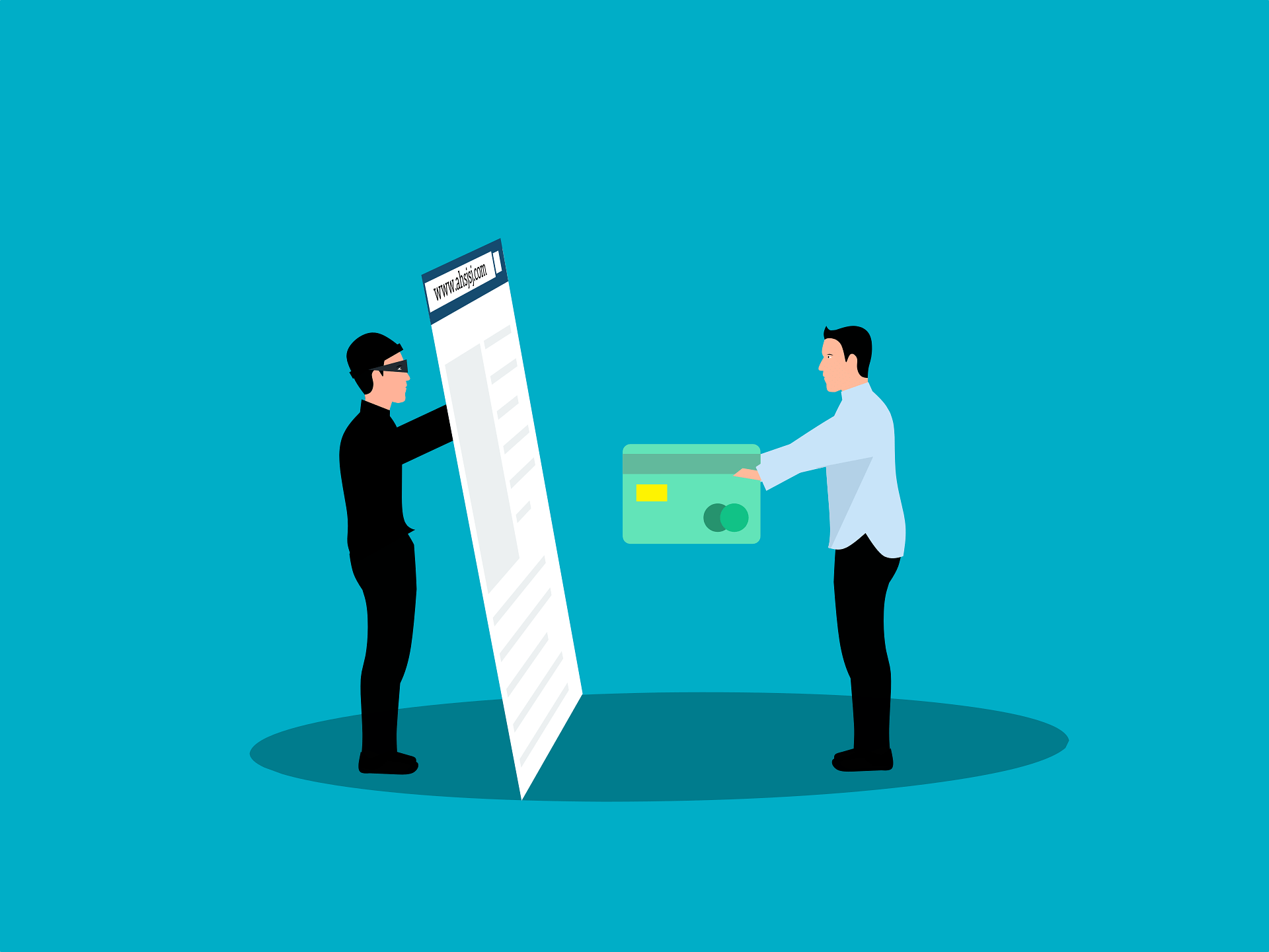
In the fast-paced world of business, invoices come and go daily — a routine part of keeping operations running smoothly. But cybercriminals know this, and they’re exploiting that routine to trick businesses into paying fake or manipulated invoices. It’s called invoice fraud, and it’s one of the fastest-growing forms of cybercrime impacting Australian businesses today.
At its core, invoice fraud is a type of scam where attackers deceive a business into transferring money to the wrong account. They do this by impersonating a trusted supplier, vendor, or even someone within your own organisation. The attack is often so subtle and well-timed that by the time it’s detected, the money is long gone.
But how exactly does invoice fraud happen? And more importantly, how can your business avoid becoming the next victim?
Invoice fraud isn’t carried out by amateurs — it’s typically orchestrated by highly organised cybercriminals who understand how businesses operate. They don’t just send a dodgy email and hope for the best. Instead, they plan, research, and strike at the most opportune moment.
Let’s break it down.
In many cases, the attack begins with email compromise. A hacker might gain access to a supplier’s inbox or spoof a legitimate email address so that it appears authentic. From there, they carefully monitor communication patterns, looking for an opportunity — like a large invoice due soon.
Then comes the clever part: they create a replica of a legitimate invoice, but with one critical difference — the bank account details are changed. The altered invoice is then sent to your accounts department, often accompanied by a convincingly written message that mimics your supplier’s tone, formatting, and signature.
Because the invoice looks expected, seems routine, and comes from a “trusted” source, it gets processed and paid. By the time someone realises the funds never reached the actual supplier, it’s often too late to recover the money.
Invoice fraud isn’t a one-size-fits-all threat. It comes in multiple flavours, each with its own level of sophistication. Here are some of the most common variations:
This is where fraudsters hack or spoof a legitimate business email account to send fraudulent invoices. Often, the attacker will lurk in the background, silently watching communication between your business and a supplier until the perfect moment arises.
In these cases, a scammer pretends to be a supplier and emails your finance team requesting a change to their payment details — perhaps claiming they’ve switched banks. These messages are often so well-crafted they pass casual scrutiny.
Sometimes, invoice fraud comes from within. A dishonest employee might create a fake supplier or manipulate invoice records to funnel money to an account they control. These schemes can go undetected for months without regular audits in place.
Here, the attacker doesn’t create an invoice — they just intercept one in transit. If your supplier emails you a PDF invoice, a hacker could catch it, modify the payment details, and resend it. Everything else looks correct — company logo, due date, line items — except the bank account.
Large enterprises often have dedicated fraud teams and sophisticated systems to detect anomalies. Small to medium businesses, on the other hand, often operate on trust, speed, and limited internal resources — and that’s exactly what attackers exploit.
You might think, “Why would someone target my small business?” The truth is, you’re the perfect target: big enough to process regular payments but small enough to have limited cybersecurity protocols in place. According to Scamwatch, false billing scams cost Australian businesses over $23 million in 2023 — and many of those businesses were SMEs.
Recognising invoice fraud before money changes hands is the key to prevention. Here are some subtle signs that something isn’t quite right:
Even one of these signs should trigger a second look — and a verification call.
While there’s no silver bullet, combining smart processes with the right technology makes a huge difference. Here's how you can reduce the risk:
Start by putting a multi-step verification process in place. Any time a supplier asks you to change bank details — no matter how legitimate it seems — someone from your team should independently verify the request by phone using previously known contact details. Never rely solely on the contact information provided in the email.
Next, educate your team — especially accounts payable and finance staff. These are the people most often targeted, and the more they understand what to watch for, the better your defence.
Technology also plays a critical role. At BIT365, we recommend clients use secure email gateways like Avanan, which provide built-in protection against phishing, spoofing, and business email compromise attempts. Coupled with endpoint protection like Huntress, your attack surface is significantly reduced.
Finally, enforce approval workflows. No large payment should ever go out without dual approval, especially when new payment instructions are involved. A small delay is a small price to pay compared to losing tens of thousands of dollars.
If you suspect your business has fallen victim to invoice fraud, don’t panic — but act immediately.
First, contact your bank to try and halt the transaction. Time is critical here. Some financial institutions have fraud teams who can attempt to claw back the funds if caught early.
Second, report the incident to authorities. This includes the ACCC via Scamwatch, the Australian Cyber Security Centre (ACSC), and your local police. These reports help track larger fraud operations and may support your case with insurers.
Finally, take a step back and review your processes. Could this have been prevented? What internal changes need to happen? This is where a cyber incident response plan becomes vital — knowing what steps to take and who is responsible reduces downtime and limits further damage.
Invoice fraud isn’t just a technical issue — it’s a human one. It targets your people, your trust, and your everyday processes. But with the right training, technology, and mindset, it’s a risk you can manage.
At BIT365, we work closely with Australian businesses to harden their cybersecurity posture and create practical defences against invoice fraud and other evolving threats. From email protection and endpoint security to awareness training and response planning, we’ve got your back.
If you’re unsure whether your accounts processes are secure — or if you want a second pair of eyes on your payment procedures — reach out. We’re here to help you keep your business safe, one invoice at a time.

Got IT issues slowing you down? We provide both on-site and remote support across Australia, so help is never far away.
BIT365 offers a full range of managed IT services, including cybersecurity, cloud solutions, Microsoft 365 support, data backup, and on-site or remote tech support for businesses across Australia.
No. While we have a strong presence in Western Sydney, BIT365 supports businesses nationwide — delivering reliable IT solutions both remotely and on-site.
We pride ourselves on fast response times. With remote access tools and on-site technicians, BIT365 can often resolve issues the same day, keeping your business running smoothly.
BIT365 combines local expertise with enterprise-grade solutions. We’re proactive, not just reactive — preventing issues before they impact your business. Plus, our friendly team explains IT in plain English, so you always know what’s happening.
